ngrep命令用法
ngrep 是grep(在文本中搜索字符串的工具)的网络版,他力求更多的grep特征,用于搜寻指定的数据包。正由于安装ngrep需用到libpcap库, 所以支持大量的操作系统和网络协议。能识别TCP、UDP和ICMP包,理解bpf的过滤机制。
语法
ngrep <-LhNXViwqpevxlDtTRM> <-IO pcap_dump> <-n num> <-d dev> <-A num>
<-s snaplen> <-S limitlen> <-W normal|byline|single|none> <-c cols>
<-P char> <-F file> <match expression> <bpf filter>
选项
-h is help/usage -V is version information -q is be quiet (don't print packet reception hash marks)静默模式,如果没有此开关,未匹配的数据包都以“#”显示 -e is show empty packets 显示空数据包 -i is ignore case 忽略大小写 -v is invert match 反转匹配 -R is don't do privilege revocation logic -x is print in alternate hexdump format 以16进制格式显示 -X is interpret match expression as hexadecimal 以16进制格式匹配 -w is word-regex (expression must match as a word) 整字匹配 -p is don't go into promiscuous mode 不使用混杂模式 -l is make stdout line buffered -D is replay pcap_dumps with their recorded time intervals -t is print timestamp every time a packet is matched在每个匹配的包之前显示时间戳 -T is print delta timestamp every time a packet is matched显示上一个匹配的数据包之间的时间间隔 -M is don't do multi-line match (do single-line match instead)仅进行单行匹配 -I is read packet stream from pcap format file pcap_dump 从文件中读取数据进行匹配 -O is dump matched packets in pcap format to pcap_dump 将匹配的数据保存到文件 -n is look at only num packets 仅捕获指定数目的数据包进行查看 -A is dump num packets after a match匹配到数据包后Dump随后的指定数目的数据包 -s is set the bpf caplen -S is set the limitlen on matched packets -W is set the dump format (normal, byline, single, none) 设置显示格式byline将解析包中的换行符 -c is force the column width to the specified size 强制显示列的宽度 -P is set the non-printable display char to what is specified -F is read the bpf filter from the specified file 使用文件中定义的bpf(Berkeley Packet Filter) -N is show sub protocol number 显示由IANA定义的子协议号 -d is use specified device (index) instead of the pcap default
Allowable primitives are:
dst host host
True if the IP destination field of the packet is host, which may be either an address or a name.
src host host
True if the IP source field of the packet is host.
host host
True if either the IP source or destination of the packet is host. Any of the above host expressions can be prepended with the
keywords, ip, arp, or rarp as in:
ip host host
which is equivalent to:
ether dst ehost
True if the ethernet destination address is ehost. Ehost may be either a name from /etc/ethers or a number (see ethers(3N) for
numeric format).
ether src ehost
True if the ethernet source address is ehost.
ether host ehost
True if either the ethernet source or destination address is ehost.
gateway host
True if the packet used host as a gateway. I.e., the ethernet source or destination address was host but neither the IP source
nor the IP destination was host. Host must be a name and must be found in both /etc/hosts and /etc/ethers. (An equivalent
expression is
ether host ehost and not host host
which can be used with either names or numbers for host / ehost.)
dst net net
True if the IP destination address of the packet has a network number of net. Net may be either a name from /etc/networks or a
network number (see networks(4) for details).
src net net
True if the IP source address of the packet has a network number of net.
net net
True if either the IP source or destination address of the packet has a network number of net.
net net mask mask
True if the IP address matches net with the specific netmask. May be qualified with src or dst.
net net/len
True if the IP address matches net a netmask len bits wide. May be qualified with src or dst.
dst port port
True if the packet is ip/tcp or ip/udp and has a destination port value of port. The port can be a number or a name used in
/etc/services (see tcp(4P) and udp(4P)). If a name is used, both the port number and protocol are checked. If a number or
ambiguous name is used, only the port number is checked (e.g., dst port 513 will print both tcp/login traffic and udp/who traf-
fic, and port domain will print both tcp/domain and udp/domain traffic).
src port port
True if the packet has a source port value of port.
port port
True if either the source or destination port of the packet is port. Any of the above port expressions can be prepended with
the keywords, tcp or udp, as in:
tcp src port port
which matches only tcp packets whose source port is port.
less length
True if the packet has a length less than or equal to length. This is equivalent to:
len <= length.
greater length
True if the packet has a length greater than or equal to length. This is equivalent to:
len >= length.
ip proto protocol
True if the packet is an ip packet (see ip(4P)) of protocol type protocol. Protocol can be a number or one of the names tcp,
udp or icmp. Note that the identifiers tcp and udp are also keywords and must be escaped via backslash (\), which is \\ in the
C-shell.
ip broadcast
True if the packet is an IP broadcast packet. It checks for both the all-zeroes and all-ones broadcast conventions, and looks
up the local subnet mask.
ip multicast
True if the packet is an IP multicast packet.
ip Abbreviation for:
ether proto ip
tcp, udp, icmp
Abbreviations for:
ip proto p
where p is one of the above protocols.
实例
抓本机eth0 与192.168.1.9的通信信息,并且以行来打印出来
#ngrep -d eth0 -W byline host 192.168.1.9
抓本机与192.168.1.8的通信端口为80(本机)的信息
# ngrep -W byline host 192.168.1.8 and port 80
抓本机与192.168.1.8和192.168.1.9的通信,并且本地端口为80
#ngrep -W byline host 192.168.1.8 or host 192.168.1.9 port 80
抓udp包
#ngrep host 192.168.1.8 udp
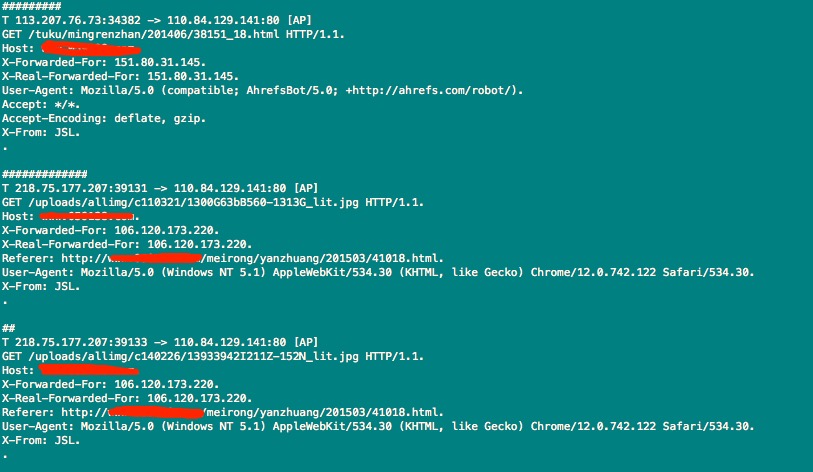
统计请求头长度
# ngrep -W byline 'GET /' 'tcp and dst port 80' -d eth1 | awk -v RS="#+" -v FS="\n" '{ print length() }'查询一下大于 1K 的请求头
# ngrep -W byline 'GET /' 'tcp and dst port 80' -d eth1 | awk -v RS="#+" -v FS="\n" 'length() > 1000'
本文由主机测评网发布,不代表主机测评网立场,转载联系作者并注明出处:https://zhuji.jb51.net/yunwei/8122.html

